commit
9601394f3e
Se han modificado 93 ficheros con 669 adiciones y 0 borrados
+ 12
- 0
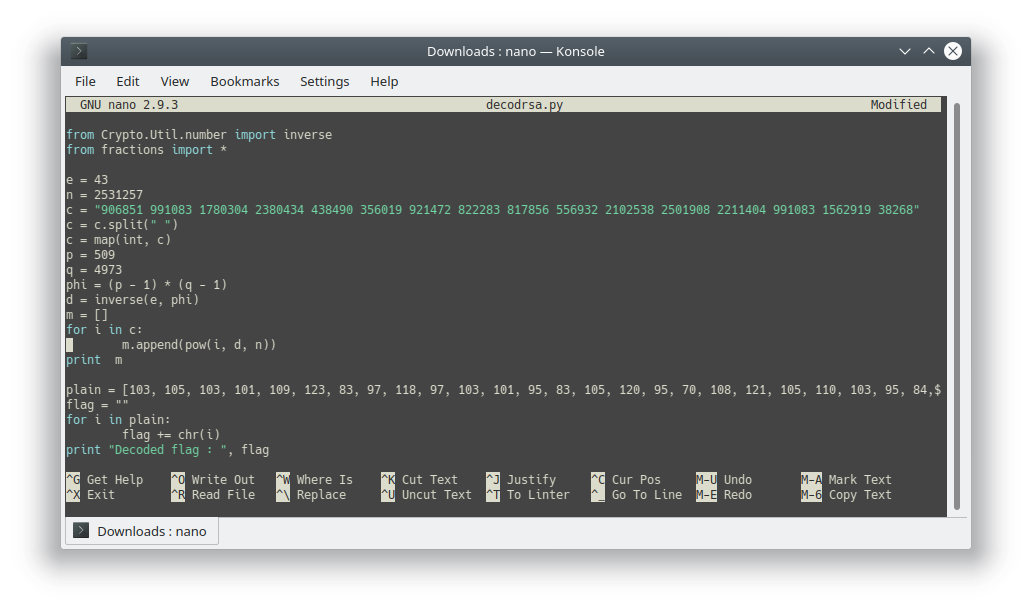
AsgamaCTF/Crypto/1byte_ROXy/decode.py
Ver fichero
+ 1
- 0
AsgamaCTF/Crypto/Capek/base
Ver fichero
+ 10
- 0
AsgamaCTF/Crypto/Capek/decryptloop.py
Ver fichero
BIN
AsgamaCTF/Reverse/XOR_in_reverse/Xrev
Ver fichero
+ 194
- 0
AsgamaCTF/Reverse/pwd/.gdb_history
Ver fichero
+ 1
- 0
AsgamaCTF/Reverse/pwd/decode.py
Ver fichero
BIN
AsgamaCTF/Reverse/pwd/pwdrev
Ver fichero
BIN
CJ2018/Pwn/Dionysus/dionysus_client
Ver fichero
BIN
CJ2018/Pwn/Dionysus/dionysus_server
Ver fichero
BIN
GKSK/Crypto/GKSK_Crypto_Service/GKSK_CRYPTO_SERVICE.zip
Ver fichero
+ 26
- 0
GKSK/Crypto/GKSK_Crypto_Service/decrypt.py
Ver fichero
+ 1
- 0
GKSK/Crypto/GKSK_Crypto_Service/flag.enc
Ver fichero
+ 97
- 0
GKSK/Crypto/GKSK_Crypto_Service/gksk_crypto_service.py
Ver fichero
+ 1
- 0
GKSK/Joy/Hack_The_Game_v0.0.1/flag.txt
Ver fichero
BIN
GKSK/Joy/Hack_The_Game_v0.0.1/version001
Ver fichero
+ 4
- 0
GKSK/Joy/Hack_The_Game_v0.0.2/cheat.py
Ver fichero
+ 12
- 0
GKSK/Joy/Hack_The_Game_v0.0.2/test.py
Ver fichero
BIN
GKSK/Joy/Hack_The_Game_v0.0.2/version002
Ver fichero
+ 3
- 0
GKSK/Pwn/World_war/.gdb_history
Ver fichero
+ 15
- 0
GKSK/Pwn/World_war/payload.py
Ver fichero
+ 1
- 0
GKSK/Pwn/World_war/peda-session-world_war.txt
Ver fichero
BIN
GKSK/Pwn/World_war/world_war
Ver fichero
BIN
GKSK/Reverse/Decimal1.0/Decimal_1.0
Ver fichero
+ 35
- 0
IDCC/Crypto/DecryptME/decrypt.py
Ver fichero
+ 1
- 0
IDCC/Crypto/DecryptME/enkripsi
Ver fichero
+ 35
- 0
IDCC/Crypto/DecryptME/test.py
Ver fichero
+ 29
- 0
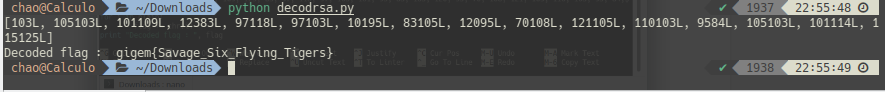
SlashRoot/Crypto/RSA_Token_Generator/payload.py
Ver fichero
BIN
TAMUCTF/Crypto/RSAaaay/Screenshot_20190302_214809.png
Ver fichero
BIN
TAMUCTF/Crypto/RSAaaay/Screenshot_20190302_222836.png
Ver fichero
BIN
TAMUCTF/Crypto/RSAaaay/Screenshot_20190302_223153.png
Ver fichero
BIN
TAMUCTF/Crypto/RSAaaay/Screenshot_20190302_224641.png
Ver fichero
BIN
TAMUCTF/Crypto/RSAaaay/Screenshot_20190302_224730.png
Ver fichero
BIN
TAMUCTF/Crypto/RSAaaay/Screenshot_20190302_225328.png
Ver fichero
BIN
TAMUCTF/Crypto/RSAaaay/Screenshot_20190302_225608.png
Ver fichero
BIN
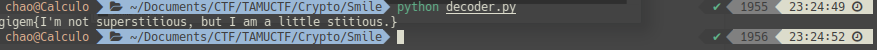
TAMUCTF/Crypto/Smile/Screenshot_20190302_231451.png
Ver fichero
BIN
TAMUCTF/Crypto/Smile/Screenshot_20190302_231606.png
Ver fichero
BIN
TAMUCTF/Crypto/Smile/Screenshot_20190302_232351.png
Ver fichero
BIN
TAMUCTF/Crypto/Smile/Screenshot_20190302_232540.png
Ver fichero
+ 13
- 0
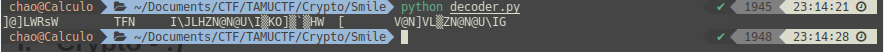
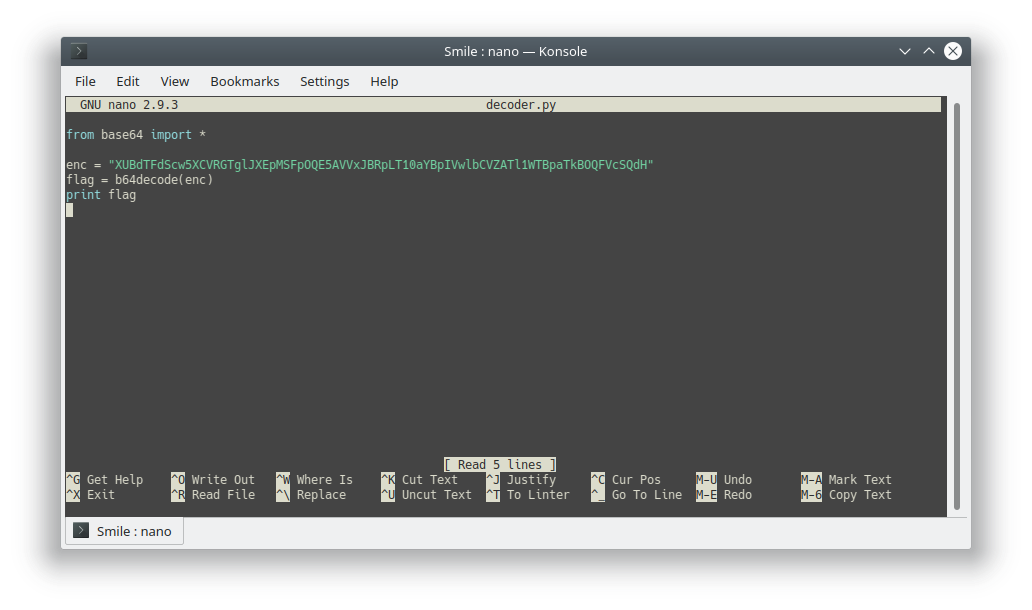
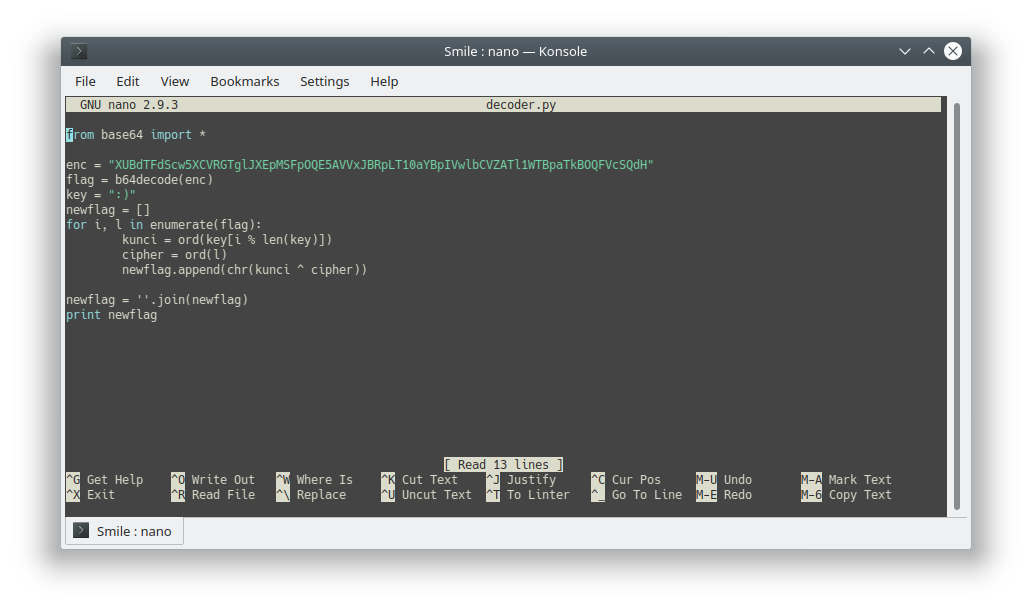
TAMUCTF/Crypto/Smile/decoder.py
Ver fichero
BIN
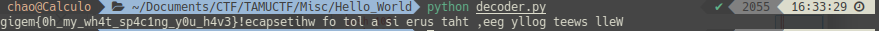
TAMUCTF/Misc/Hello_World/Screenshot_20190303_161722.png
Ver fichero
BIN
TAMUCTF/Misc/Hello_World/Screenshot_20190303_163026.png
Ver fichero
BIN
TAMUCTF/Misc/Hello_World/Screenshot_20190303_163249.png
Ver fichero
BIN
TAMUCTF/Misc/Hello_World/Screenshot_20190303_163350.png
Ver fichero
+ 99
- 0
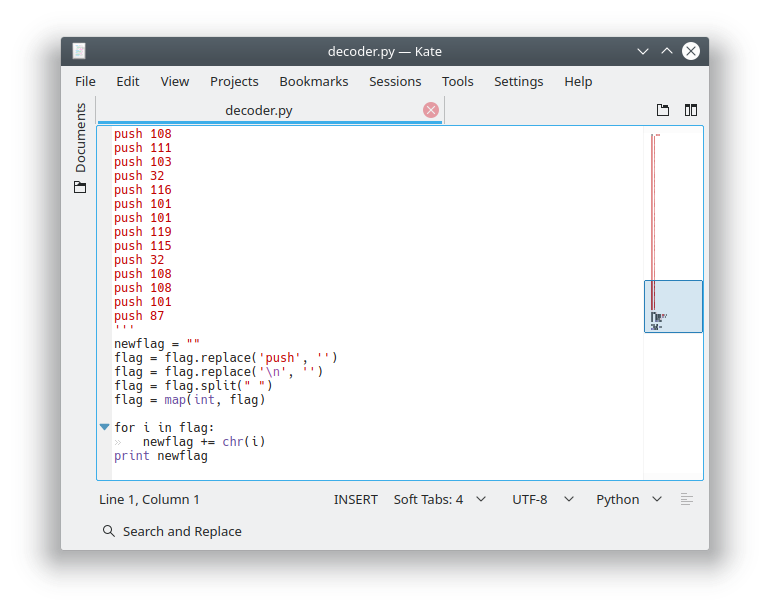
TAMUCTF/Misc/Hello_World/decoder.py
Ver fichero
BIN
TAMUCTF/Misc/I_heard_you_like_files/Screenshot_20190303_155553.png
Ver fichero
BIN
TAMUCTF/Misc/I_heard_you_like_files/Screenshot_20190303_160033.png
Ver fichero
BIN
TAMUCTF/Misc/I_heard_you_like_files/Screenshot_20190303_160404.png
Ver fichero
BIN
TAMUCTF/Misc/I_heard_you_like_files/Screenshot_20190303_160559.png
Ver fichero
BIN
TAMUCTF/Misc/I_heard_you_like_files/Screenshot_20190303_160905.png
Ver fichero
BIN
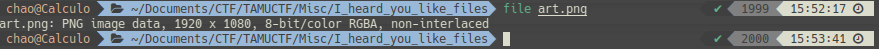
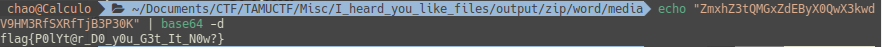
TAMUCTF/Misc/I_heard_you_like_files/art.png
Ver fichero
+ 27
- 0
TAMUCTF/Misc/I_heard_you_like_files/output/audit.txt
Ver fichero
BIN
TAMUCTF/Misc/I_heard_you_like_files/output/pdf/00006657.pdf
Ver fichero
BIN
TAMUCTF/Misc/I_heard_you_like_files/output/png/00000000.png
Ver fichero
BIN
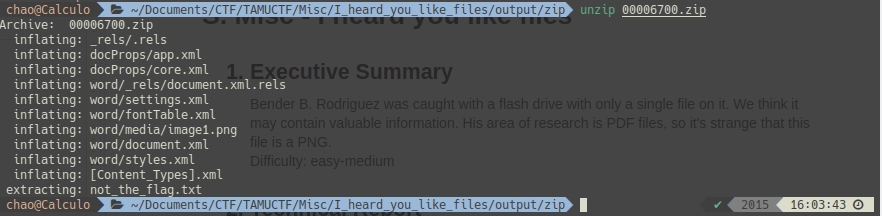
TAMUCTF/Misc/I_heard_you_like_files/output/zip/00006700.zip
Ver fichero
+ 3
- 0
TAMUCTF/Misc/I_heard_you_like_files/output/zip/[Content_Types].xml
Ver fichero
+ 3
- 0
TAMUCTF/Misc/I_heard_you_like_files/output/zip/_rels/.rels
Ver fichero
+ 2
- 0
TAMUCTF/Misc/I_heard_you_like_files/output/zip/docProps/app.xml
Ver fichero
+ 2
- 0
TAMUCTF/Misc/I_heard_you_like_files/output/zip/docProps/core.xml
Ver fichero
+ 1
- 0
TAMUCTF/Misc/I_heard_you_like_files/output/zip/not_the_flag.txt
Ver fichero
+ 3
- 0
TAMUCTF/Misc/I_heard_you_like_files/output/zip/word/_rels/document.xml.rels
Ver fichero
+ 2
- 0
TAMUCTF/Misc/I_heard_you_like_files/output/zip/word/document.xml
Ver fichero
+ 2
- 0
TAMUCTF/Misc/I_heard_you_like_files/output/zip/word/fontTable.xml
Ver fichero
BIN
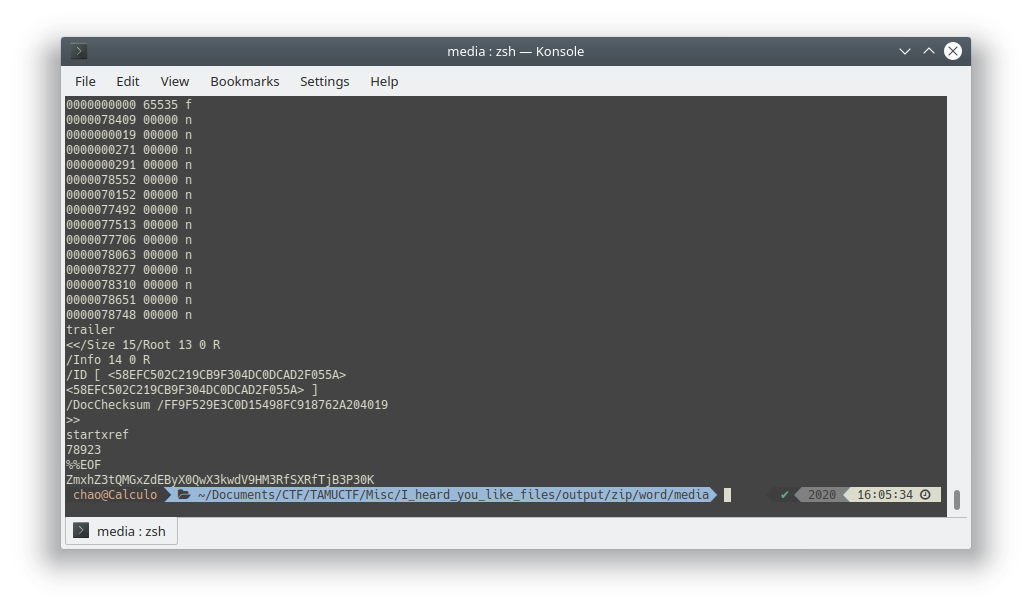
TAMUCTF/Misc/I_heard_you_like_files/output/zip/word/media/image1.png
Ver fichero
+ 2
- 0
TAMUCTF/Misc/I_heard_you_like_files/output/zip/word/settings.xml
Ver fichero
+ 2
- 0
TAMUCTF/Misc/I_heard_you_like_files/output/zip/word/styles.xml
Ver fichero
+ 10
- 0
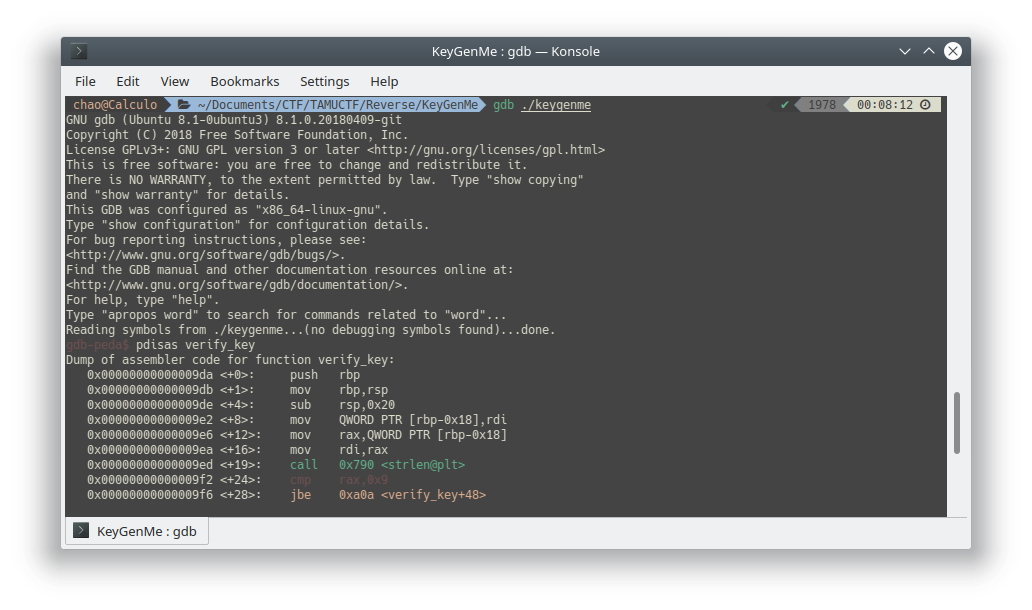
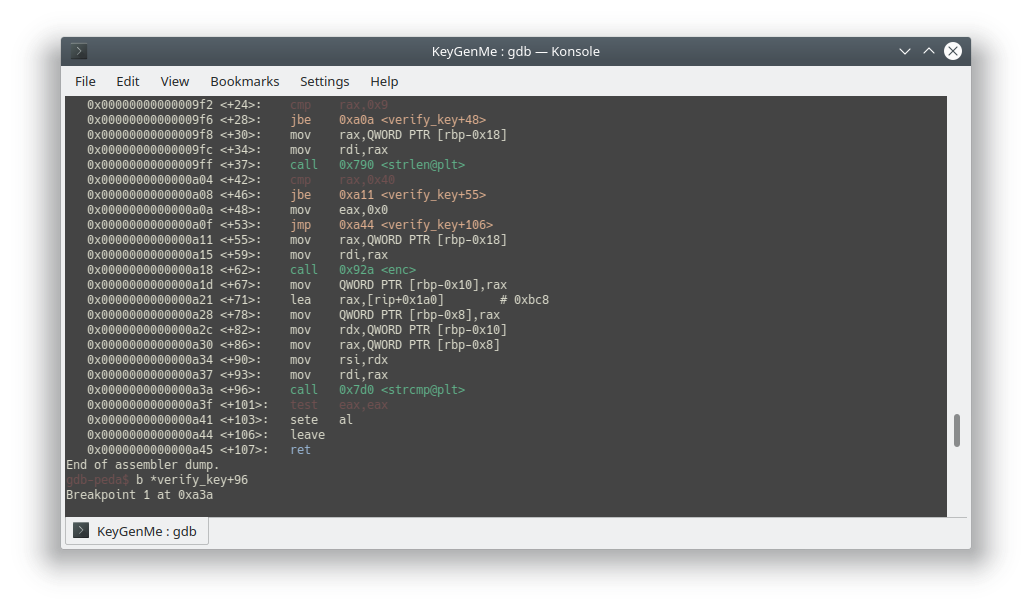
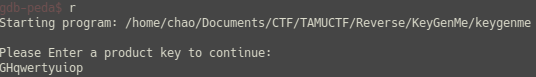
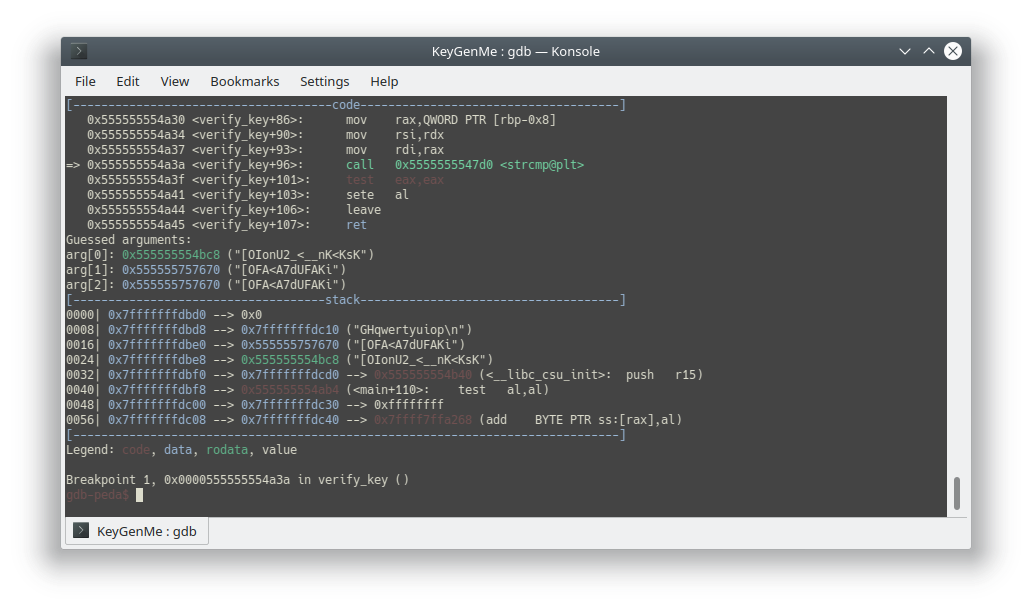
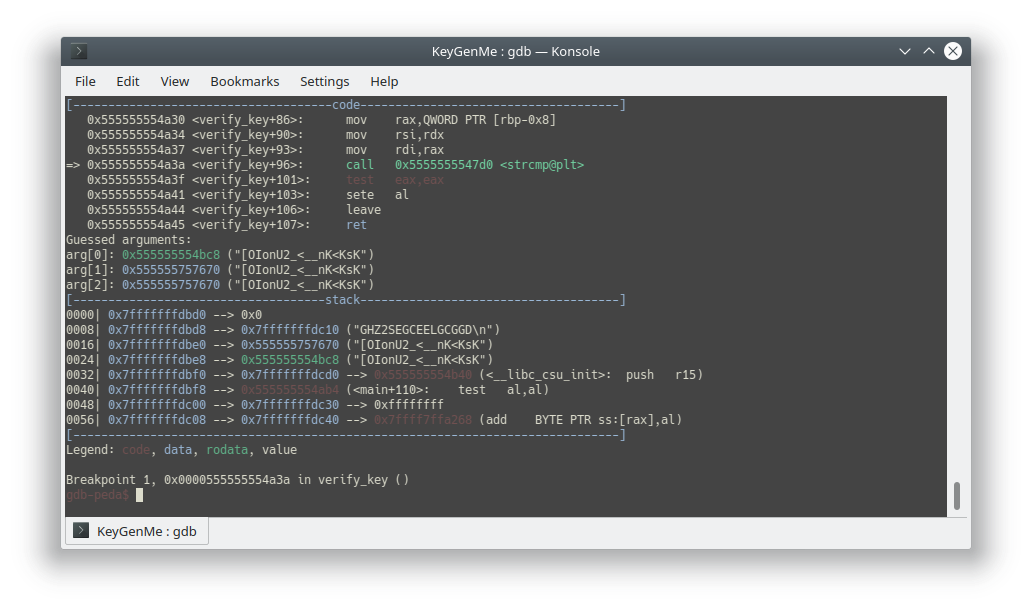
TAMUCTF/Reverse/KeyGenMe/.gdb_history
Ver fichero
BIN
TAMUCTF/Reverse/KeyGenMe/Screenshot_20190302_233546.png
Ver fichero
BIN
TAMUCTF/Reverse/KeyGenMe/Screenshot_20190302_233856.png
Ver fichero
BIN
TAMUCTF/Reverse/KeyGenMe/Screenshot_20190302_234341.png
Ver fichero
BIN
TAMUCTF/Reverse/KeyGenMe/Screenshot_20190302_234432.png
Ver fichero
BIN
TAMUCTF/Reverse/KeyGenMe/Screenshot_20190302_235534.png
Ver fichero
BIN
TAMUCTF/Reverse/KeyGenMe/Screenshot_20190303_000342.png
Ver fichero
BIN
TAMUCTF/Reverse/KeyGenMe/Screenshot_20190303_000843.png
Ver fichero
BIN
TAMUCTF/Reverse/KeyGenMe/Screenshot_20190303_001206.png
Ver fichero
BIN
TAMUCTF/Reverse/KeyGenMe/Screenshot_20190303_001324.png
Ver fichero
BIN
TAMUCTF/Reverse/KeyGenMe/Screenshot_20190303_001417.png
Ver fichero
BIN
TAMUCTF/Reverse/KeyGenMe/Screenshot_20190303_001835.png
Ver fichero
BIN
TAMUCTF/Reverse/KeyGenMe/Screenshot_20190303_002033.png
Ver fichero
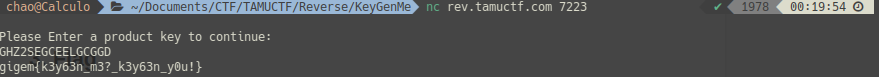
+ 20
- 0
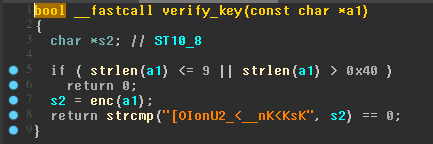
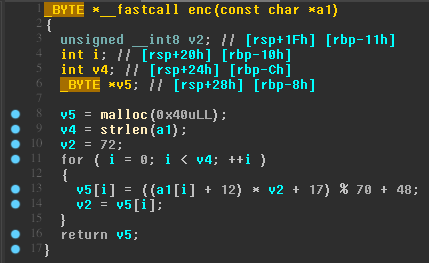
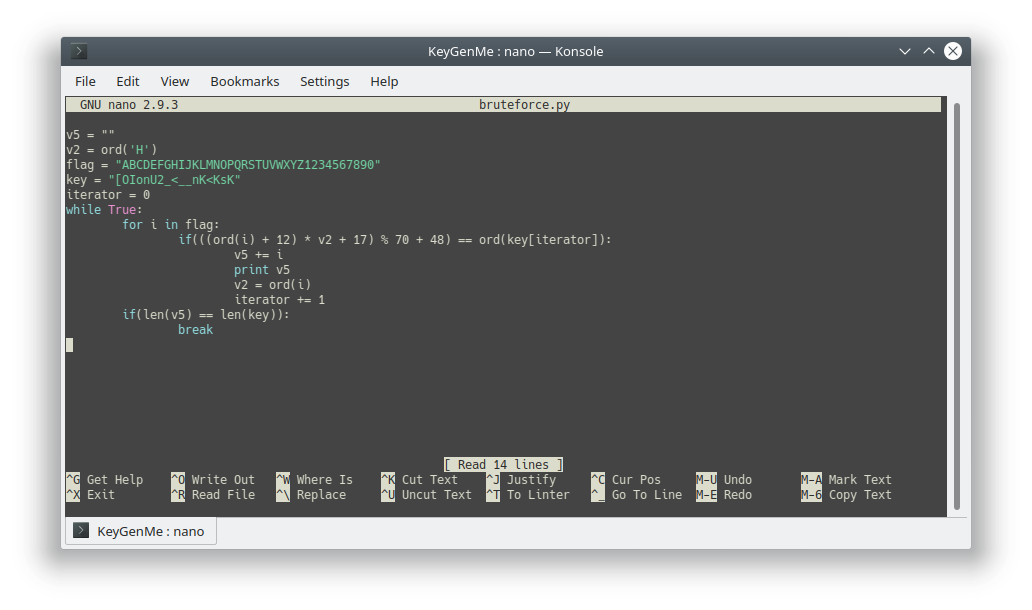
TAMUCTF/Reverse/KeyGenMe/bruteforce.py
Ver fichero
BIN
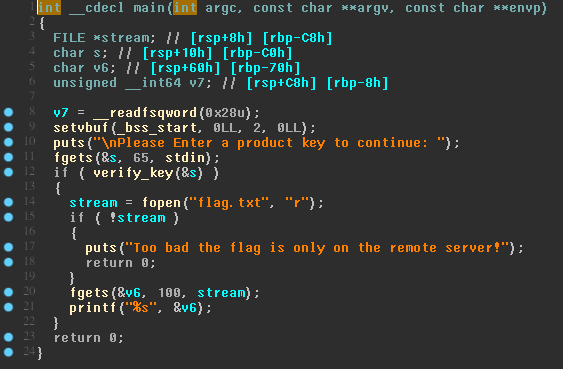
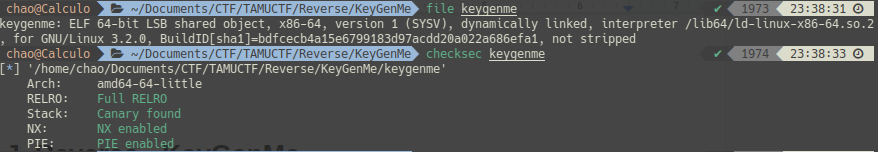
TAMUCTF/Reverse/KeyGenMe/keygenme
Ver fichero
BIN
TAMUCTF/Secure_Coding/SQL/Screenshot_20190303_153550.png
Ver fichero
BIN
TAMUCTF/Secure_Coding/SQL/Screenshot_20190303_153910.png
Ver fichero
BIN
TAMUCTF/Secure_Coding/SQL/Screenshot_20190303_154148.png
Ver fichero
BIN
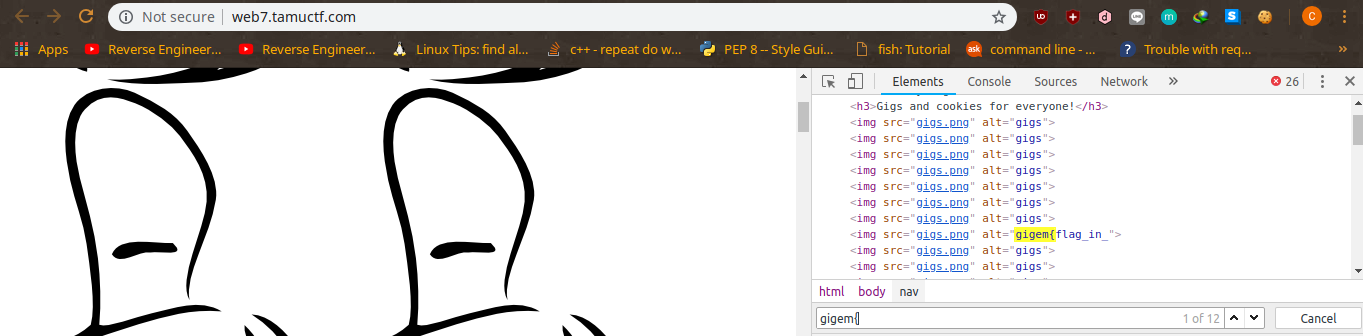
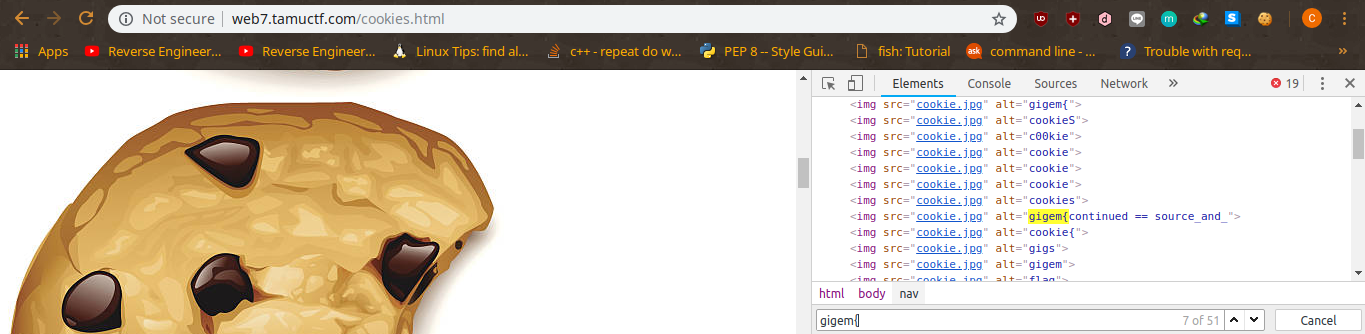
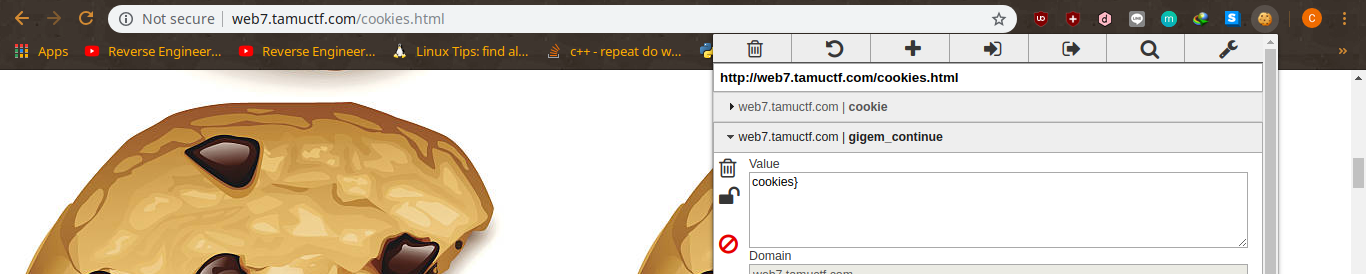
TAMUCTF/Web/Many_Gigems_To_You/Screenshot_20190302_202844.png
Ver fichero
BIN
TAMUCTF/Web/Many_Gigems_To_You/Screenshot_20190302_203307.png
Ver fichero
BIN
TAMUCTF/Web/Many_Gigems_To_You/Screenshot_20190302_203644.png
Ver fichero
BIN
TAMUCTF/Web/Many_Gigems_To_You/Screenshot_20190302_203910.png
Ver fichero
BIN
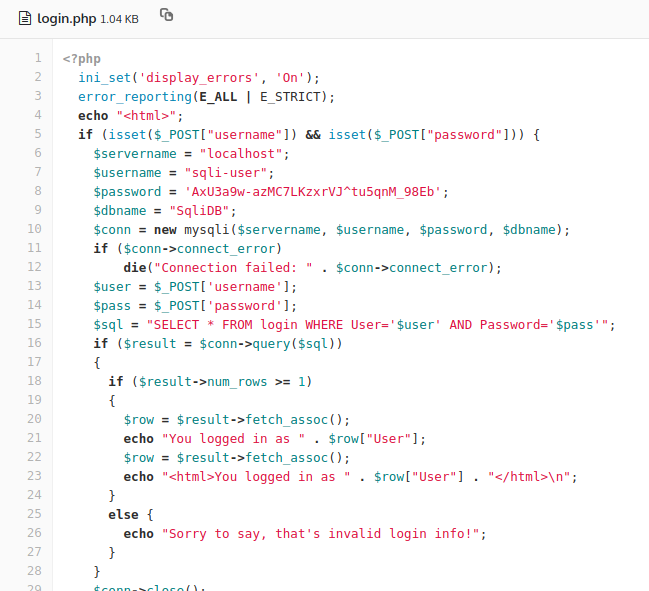
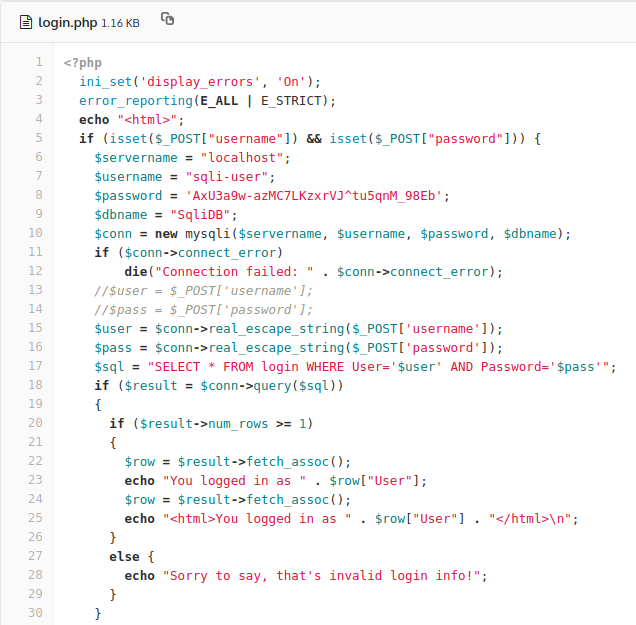
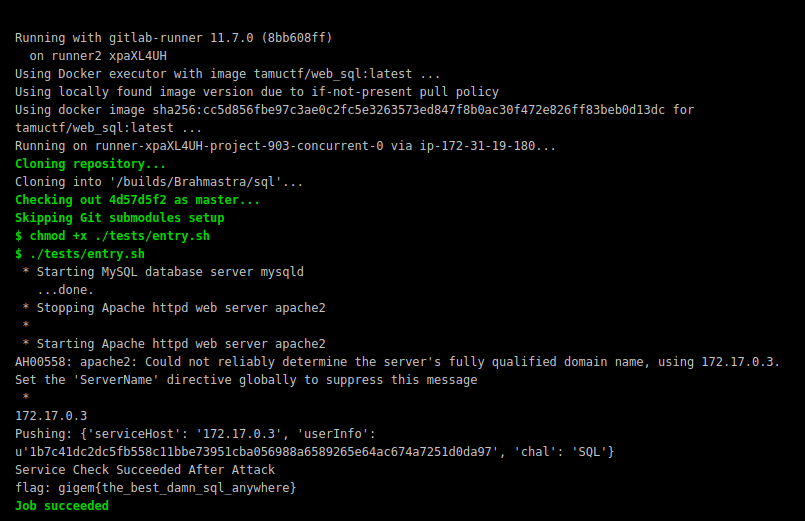
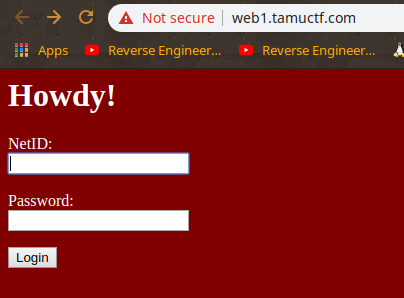
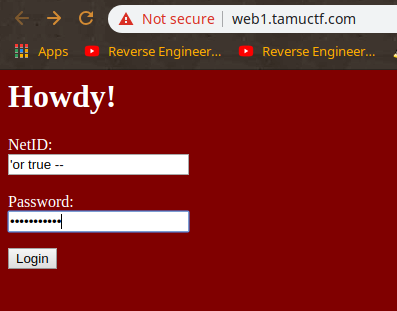
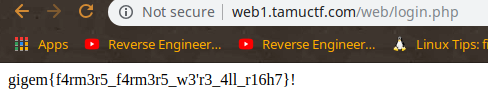
TAMUCTF/Web/Not_Another_SQLi_Challenge/Screenshot_20190302_200611.png
Ver fichero
BIN
TAMUCTF/Web/Not_Another_SQLi_Challenge/Screenshot_20190302_200703.png
Ver fichero
BIN
TAMUCTF/Web/Not_Another_SQLi_Challenge/Screenshot_20190302_200832.png
Ver fichero
BIN
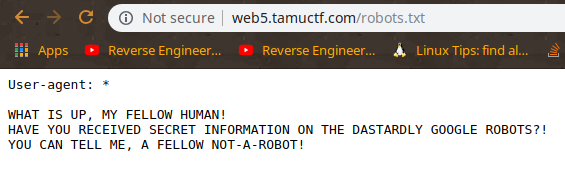
TAMUCTF/Web/Robots_Rule/Screenshot_20190302_201534.png
Ver fichero
BIN
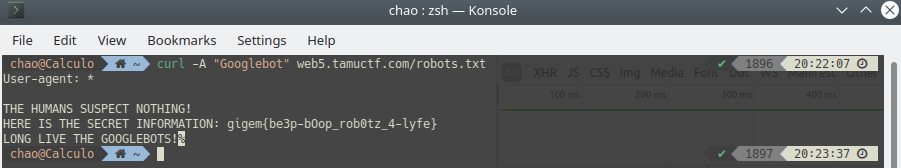
TAMUCTF/Web/Robots_Rule/Screenshot_20190302_201719.png
Ver fichero
BIN
TAMUCTF/Web/Robots_Rule/Screenshot_20190302_202358.png
Ver fichero
Cargando…